Recent events, such as the Log4Shell / Log4J vulnerability, underscore the importance of best practices for cybersecurity in software development. And, with increasing cyber attacks, it’s more important than ever that organizations can pre-empt and respond to emerging threats. A key focal point for proactive cybersecurity management is the Software Bill of Materials (SBOM). SBOM has strategic implications for managing open-source software components within a product. Furthermore, in November 2023 there were developments under President Biden Executive Orders for Cybersecurity and Artificial Intelligence and National Cybersecurity Strategy. Let’s take a look at the latest things you need to know about SBOM compliance.
The Software Supply Chain And SBOM Compliance
Modern software development hinges on the integration of open-source libraries, turning the process into a collaborative effort involving a multitude of building blocks. Additionally, open-source components bring efficiency but also introduce challenges.
The Essence of Software Bill of Materials (SBOM)
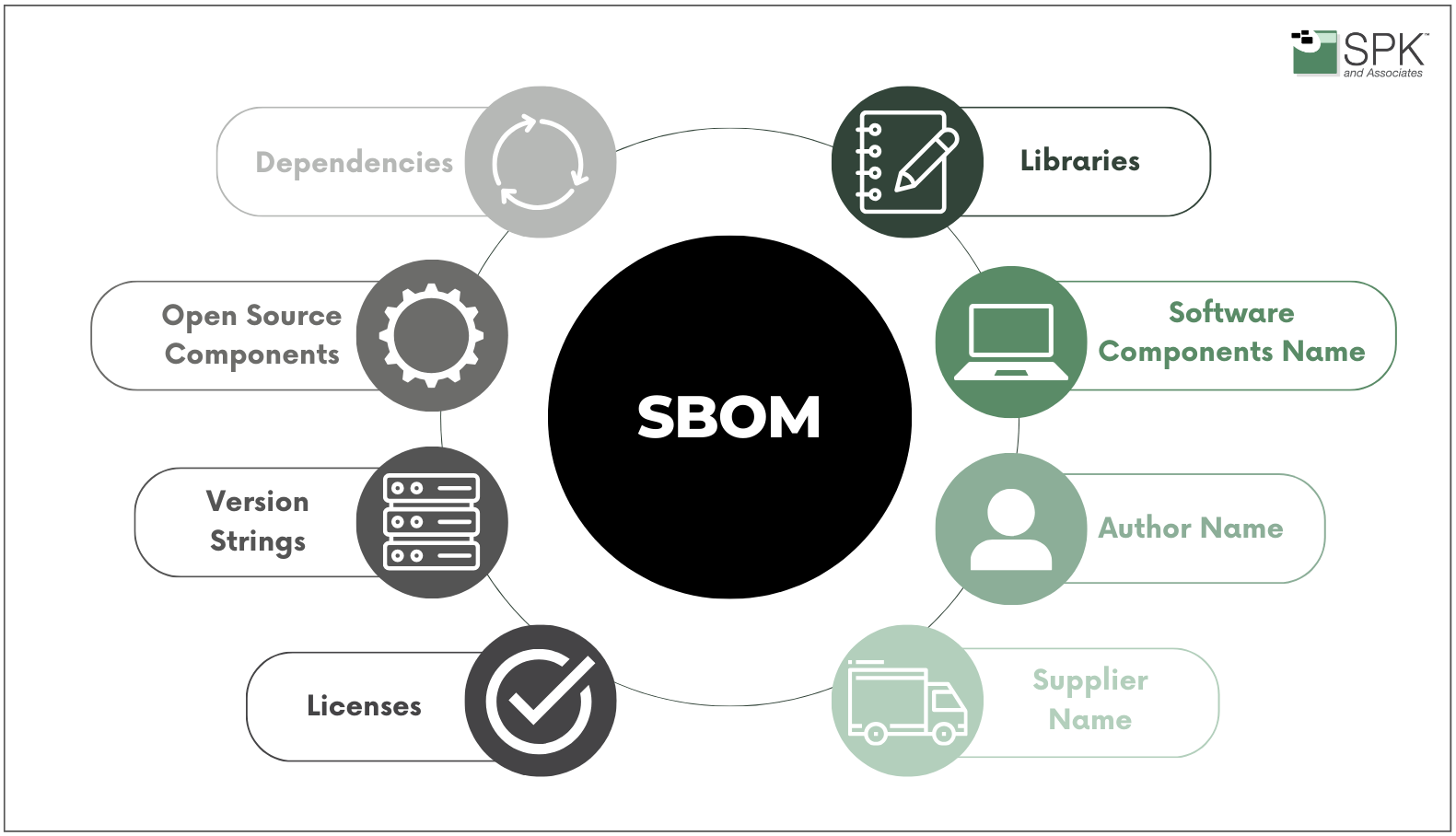
A Software Bill of Materials (SBOM) is a solution in navigating the complexities of software supply chains. Essentially, an SBOM compliance provides a detailed inventory of all components and dependencies embedded within a software application. And, for organizations, this transparency is invaluable, offering insights into the intricate web of:
- third-party modules,
- libraries,
- and frameworks that constitute the software.
Strategic Considerations for Open Source Software
As organizations contemplate their cybersecurity strategy, focusing on open-source software becomes paramount. While Log4Shell serves as a notable example, it merely scratches the surface of the broader challenge posed by the inclusion of open-source components. So, to effectively manage this aspect, adopting strategic considerations centered around SBOM compliance is essential.
Embracing SBOM for Proactive Compliance
- Comprehensive Component Analysis: Leverage SBOM to conduct a thorough analysis of all components, identifying potential vulnerabilities and risks associated with open-source software.
- Real-time Monitoring: Implement automated tools for continuous monitoring, ensuring that any emerging vulnerabilities in open-source libraries are promptly addressed.
- Collaborative Vendor Engagement: Establish active collaboration with software vendors, staying informed about updates, patches, and security enhancements related to open-source components.
- Educational Initiatives: Foster a culture of cybersecurity awareness among development teams, emphasizing the significance of scrutinizing and managing open-source software responsibly.
Navigating Compliance Challenges with SBOM
In the context of compliance challenges, SBOM becomes a linchpin for organizations aiming to adhere to industry standards and regulations. Basically, it offers a roadmap for demonstrating transparency and due diligence in managing the intricate web of open-source dependencies.
The 2023 Updates To The Biden Executive Order For SBOM Compliance
In November 2023, the Biden Executive Order received an update. Here’s what you need to know.
CISA’s Revised Draft Self-Attestation Common Form
Firstly, on November 16, 2023, CISA released a revised draft of the Common Secure Software Development Self-Attestation common form. Furthermore, this revision follows 110 comments received on the prior draft, incorporating changes responsive to industry feedback. While exemptions for “freely obtained and publicly available” software were added, the revision removes the provision allowing delegation of attestation. Organizations should stay vigilant as the final Common Form, anticipated in early 2024, may impact critical and non-critical software providers differently.
Best Practices for SBOM Consumption
Collaborating with industry partners in the “Enduring Security Framework,” CISA and the NSA published a cybersecurity technical report on November 9, 2023. Titled “Securing The Software Supply Chain: Recommended Practices for Software Bill of Materials Consumption,” the report offers valuable insights for SBOM consumers. Additionally, it emphasizes:
- Operationalizing and scaling SBOM use.
- Turning SBOMs into Risk Information.
- Creating risk scores based on factors like Vulnerabilities, License, Community, and Dependencies.
FAR Council Extends Comment Period
Next, the FAR Council proposed two new FAR cybersecurity rules on October 3, 2023, addressing cyber threat reporting and standardizing cybersecurity requirements:
- One clause will apply to contracts using cloud computing services.
- One will apply to contracts using non-cloud computing (i.e., on-premises) services.
Furthermore, responding to industry concerns, the original 60-day comment period was extended until February 4, 2024. Federal contractors should stay informed and actively participate in the comment process to shape the impact of these regulations on their operations.
OMB’s Draft Guidance on AI Implementation
On November 1, 2023, the Office of Management and Budget (OMB) released draft guidance for agencies to implement the Artificial Intelligence (AI) Executive Order. The draft emphasizes:
- Designating Chief AI Officers.
- Removing barriers to responsible AI use.
- Managing risk in federal AI procurement.
Moreover, agencies are urged to prioritize AI in IT infrastructure and ensure cybersecurity processes align with AI applications.
CISA’s AI Roadmap
Lastly, CISA’s Artificial Intelligence roadmap, unveiled on November 14, 2023, outlines strategic efforts, including responsibly using AI for cyber defense and protecting critical infrastructure. Plus, within the roadmap, CISA commits to:
- incorporating AI systems into its Secure By Design Initiative.
- Evaluating SBOM toolchains.
- Confirming AI software coverage in SBOM assessments.
At SPK we highly recommend utilizing tools like GitLab for managing DevSecOps. You can learn more about GitLab and why they were named a Leader twice in 2023 for their AI-powered DevSecOps platform.
SBOM Compliance Supports Cybersecurity Resilience
As organizations fortify their cybersecurity defenses, the strategic integration of SBOM emerges as a cornerstone. So, by embracing SBOM compliance practices, organizations not only enhance their understanding of the software supply chain but also proactively manage and mitigate risks associated with open-source software. While incidents like Log4Shell provide valuable lessons, the broader focus on SBOM empowers organizations to navigate the ever-evolving landscape of cybersecurity with resilience and compliance at its core.
If you need support with cybersecurity in your organization, our team of software cybersecurity experts can help. Contact us here for a no obligation discussion.