When working in a technology-driven environment, it is common to encounter cybersecurity threats. Although it may appear daunting, there are ways to ensure preparation for incoming risks. One of the ways to do this is by implementing a process called threat modeling. This is even more important when producing products that contain software.
What is Threat Modeling in Cybersecurity?
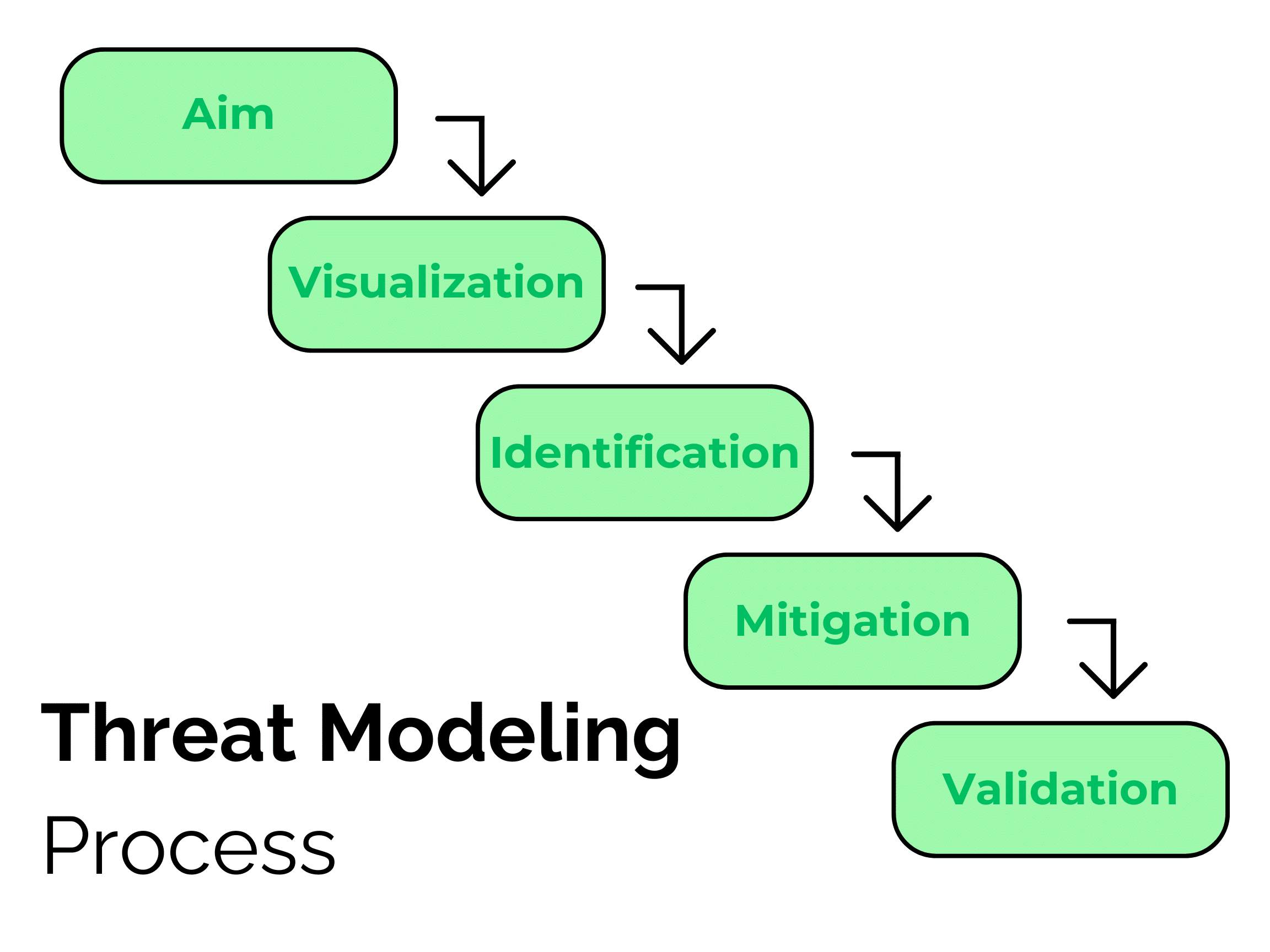
Threat modeling can be defined as a group of actions designed to enhance security for a system, or more commonly a product. These actions often aim to detect potential risks and develop countermeasures to lessen or prevent the risks. Additionally, threat models utilize a comprehensible sequence to organize all the data influencing an application’s security. The process typically includes the following steps:
- Define the scope of the system you are working with including a description of its architecture, making sure to identify any weaknesses.
- Recognize important assets you aim to protect such as intellectual property or significant data.
- Identify potential threats that could compromise the system such as a hacker or a system failure, as well as the possibility of these risks occurring.
- Effectively mitigate threats by implementing strategies such as updating security controls.
- Verify the threats have been successfully mitigated and document your process.
How Does It Work?
Now that we have defined threat modeling, let’s dive into what the framework aims to achieve. Its goal is to recognize and eliminate potential threats to a system. These threats can be anything from a malicious attack or an incidental event such as storage failure. Equally important, these risks typically threaten software applications, IoT devices, and business processes. Threat modeling seeks to protect these types of systems.
When implementing threat modeling, it is important to reiterate the process. Continuously updating the steps as a system evolves or new threats emerge is the key to preventing risks. As threats become increasingly dangerous, refining the model becomes imminent. Here are a few particular occurrences in which it should be reformed:
- When a new system feature is released
- When the infrastructure of the system is altered
- When a security risk has violated the system
Why is It Important?
Why is threat modeling necessary? First, it is a proactive strategy to eliminate security threats. It not only eliminates risks but prevents them so organizations know how to handle threats when they occur. Secondly, it helps create well-informed decisions surrounding security. It does this by visualizing security threats and the decisions needed to protect the system from them. Lastly, it enhances the overall security of systems and processes by generating a guide for organizations to follow. Organizations create a unique list and make security decisions based on their own system needs, resulting in personalized cybersecurity. In summary, threat modeling is a reliable process that applies to various fields to eliminate security risks.
How Can SPK Help Your Organization Implement Threat Modeling?
As important as threat modeling is, it can be difficult to keep up with the continuous updates. At SPK we understand many businesses need a resource to help them keep up with their threat model. Our experts have helped Fortune 100 clients get their products to market quickly and securely with our cybersecurity and threat modeling services, as you can see from this case study. Our cybersecurity management experts can bring a deeper understanding of critical infrastructure, device security, and security policy to your organization. If you would like to learn more about the importance of cybersecurity or how we can help implement threat modeling in your organization, contact our experts today.